6 Steps to create a safe mobile app

Today, the number of smartphone users worldwide is over 3 billion, and this number is forecasted to grow by several hundred million over the next few years.
Apps are getting more ingrained in our daily and professional lives. They can do plenty of things; from executing financial transactions to uploading sensitive health data.
At Kutia, we work with start-ups and established industry leaders, designing mobile applications that make life easier for their customers. One of the most important factors we look at when building mobile apps is security – how we can protect both consumer and corporate data, while still building an application that is meaningful for both parties.
What are the security risks for mobile applications?
Threat #1 Malware
One possible threat to mobile app security is malware, which is installed on the device. Mobile devices are often configured to only allow application installation from an authorized app store (e.g., Google Play or Apple Store). With malware, a hacker places a malicious application in an authorized app store, enabling the application to be installed onto targeted devices.
Threat #2: Lost or stolen device
Another huge threat is that mobile devices could be lost, or even stolen. A person with physical access to a mobile device may try to bypass the device’s lock screen in order to access sensitive information stored on the device.
Threat #3: Code guessing
A more straight-forward approach to bypassing phone security is the Code Guessing method. In this method, the potential thief tries to crack the lock screen passcode (typically a PIN or password). This could be by brute force or by something known as “shoulder surfing”, where someone observes the device owner’s use of the lock screen passcode.
How to create a secure mobile app?
1. Source Code Encryption
As most of the code in a native mobile app are on the client side, mobile malware can easily track the bugs and vulnerabilities within the source code and design. Developers should ensure that their applications are robust enough to prevent any tampering and reverse engineering attacks. Encrypting the source code can be an ideal way to defend your application from these attacks as it ensures unreadable.
2. Secure the Data-in-transit
The sensitive information that is transmitted from the client to server needs to be protected against privacy leaks and data theft. It is highly recommended to use either an SSL or VPN tunnel, which ensures that user data is protected with strict security measures.
3. Make Provisions for Data Security
When it comes to accessing confidential data, the mobile apps are designed in a way that the unstructured data is stored in the local file system and/or database within the device storage. However, the data in the sandbox are not effectively encrypted; hence, there is a major loophole for potential vulnerabilities.
4. High-level Authentication
Developers should design the apps in such a way that it only accepts strong alphanumeric passwords. On top of that, it is better to make it mandatory for the users to change their passwords periodically. For extremely sensitive apps, you can strengthen the security with biometric authentication using fingerprints or retina scan.
5. Secure the Backend
It is essential to have security measures in place to safeguard against malicious attacks at backend servers. Most of the developers assume that only the app that has been programmed to access APIs can access it. However, you should verify all your APIs in accordance with the mobile platform you aim to code for because API authentication and transport mechanisms can deviate from one platform to another.
6. Minimize Storage of Sensitive Data
To protect sensitive data from the users, developers prefer to store the data in the device local memory. However, it is best practice to avoid storing sensitive data as it might increase the security risk. If you have no other option other than storing the data, better use encrypted data containers or key chain. Additionally, make sure to minimize the log by adding the auto-delete feature, which automatically deletes data after a certain time.
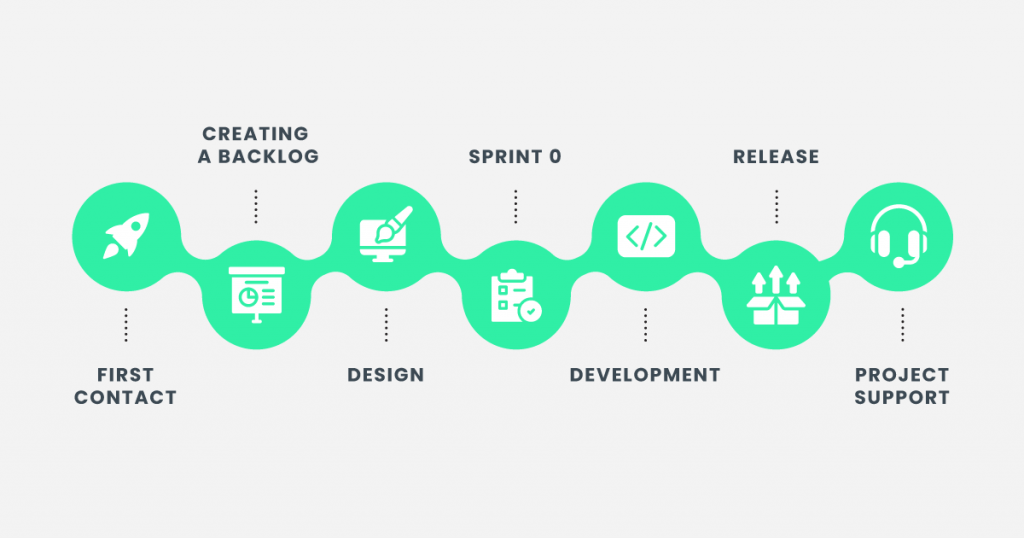
Our App Development Process
To build a safe mobile app, first, we need to have a development process that fits the needs of each project. Success within the competitive landscape of these growth projections can become a reality for your company—but only if supported by a precisely cultivated mobile app development process.
An effective app development process flow lays over seven key phases. Regardless of the size and scope of your project, we have developed a process that will make your enterprise mobile app development initiative a success.
If you’ve already made up your mind and you’re willing to build your safe app, contact us at [email protected].